You’ve probably come across this string or something similar with an IP address and found yourself wondering what it means.
That string is known as a subnet mask. But what is a subnet mask exactly, and why does it appear alongside IP addresses?
This article will walk you through everything you need to know about subnet masks.
You will take away a crystal clear understanding of the following concepts:
- What is a subnet mask
- What are subnets
- How does subnetting work
- Why subnet masks, subnets, and subnetting matter in networking
To make it easier, the article provides clear examples that demonstrate how all these pieces fit together.
Let’s begin.
Table of Contents
What is a Subnet Mask?
To understand what is a subnet mask, we’ll have to start with IP addresses.

What is an IP Address?
You know that a home address identifies a specific house within a city or a street. Similarly, an IP address string identifies a host device on a larger network.
Just as a postal address contains both the neighborhood and the exact house number, an IP address contains information about the network it belongs to as well as the unique identifier of the device itself.
For example, let‘s say your address is “123 Main Street, Springfield.” The “Springfield” part represents the network (a larger group), while “123 Main Street” pinpoints the exact location (the host).
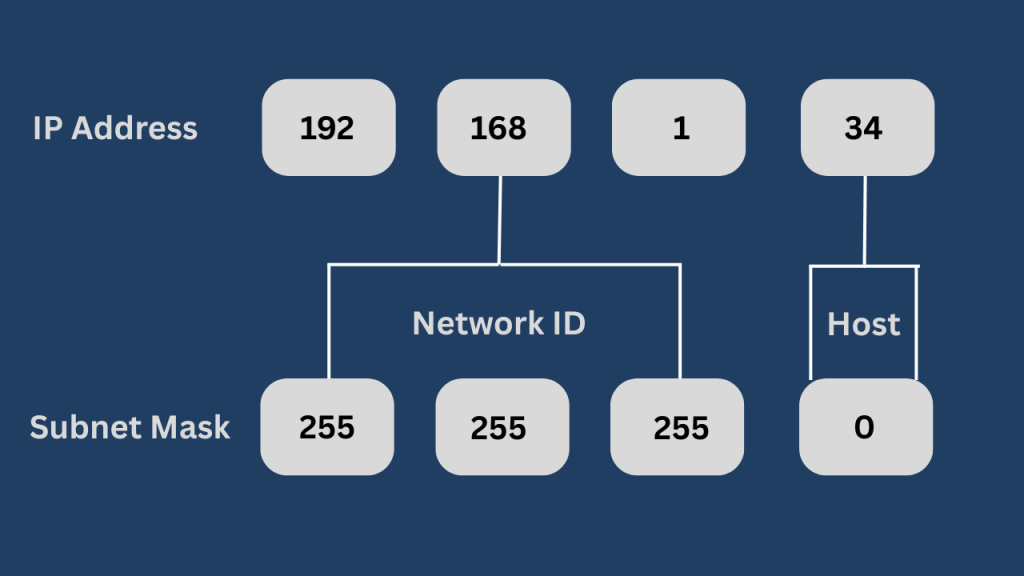
Similarly, in an IP address like 192.168.1.10, certain bits determine the network, while some bits identify the device.
Subnet Mask
However, unlike a postal address, where the separation between city and street is apparent to humans, an IP address alone doesn’t show which part is the network and which is the host.
For that, you need another 32-bit number called the subnet mask.
A subnet mask acts like a filter that tells devices how to interpret a given IP address.
It does this by using a sequence of 1s (indicating the network portion) followed by 0s (indicating the host portion).
When the IP address and subnet mask are compared using a bitwise AND operation, the result reveals the network address, while the remaining bits identify the host.
For example:
| Binary notation | ||
| IP Address | 192.168.1.10 | 11000000.10101000.00000001.00001010 |
| Subnet Mask | 255.255.255.0 | 11111111.11111111.11111111.00000000 |
Since the subnet mask has 1s in the first three octets, the first three octets of the IP address represent the network ID. It means 192.168.1 is the network ID.
The last octet (0) of the subnet mask allows for host addresses, so .10 is the specific device.
This means the given IP address belongs to a network that can contain devices from 192.168.1.1 to 192.168.1.254.
Now, this entire range of host addresses forms a subnet (we’ll get into what are subnets later).
Another example:
| Binary notation | ||
| IP Address | 10.0.0.5 | 00001010.00000000.00000000.00000101 |
| Subnet Mask | 255.0.0.0 | 11111111.00000000.00000000.00000000 |
Here, only the first octet of the subnet mask (255) is the network part, so 10. is the network.
The remaining three octets (0.0.0) allow for millions of hosts, with .5 being one of them.
And the network can contain host addresses from 10.1.0.0 to 10.255.255.255.
Here’s a more complex case:
| Binary notation | ||
| IP Address | 172.16.128.200 | 10101100.00010000.10000000.11001000 |
| Subnet Mask | 255.255.192.0 | 11111111.11111111.11000000.00000000 |
The first 18 bits (from 255.255.192.0) define the network, resulting in 172.16.128.0.
The remaining 14 bits allow for host addresses, making .200 part of a larger possible range.

Representation of a Subnet Mask
The most efficient and widely used method to represent subnet masks today is CIDR (Classless Inter-Domain Routing) notation.
Before CIDR, IPv4 relied on classful addressing, where the subnet mask was implied by the IP address itself. The first few bits of an IP address determined whether it was Class A, B, or C, and thus its default mask.
The concept of classful addressing dictated that an IP address’s inherent class automatically determined its subnet mask. No additional configuration was needed.
This system, rooted in the early days of the Internet, divided IPv4 addresses into three primary classes (A, B, C). It was on the basis of the first few bits of the address.
However, this rigid system wasted IP addresses, as networks had to fit into fixed sizes.
For example:
- Class A addresses always began with a 0 in the first bit (e.g., 1.0.0.0 to 126.0.0.0).
- Default mask: 255.0.0.0 (or /8 in CIDR terms).
This meant the first octet was the network. And the remaining three octets (16.7 million hosts) were for devices, an impractical scale for most organizations.
- Class B started with 10 in the first two bits (e.g., 128.0.0.0 to 191.255.0.0).
- Default mask: 255.255.0.0 (/16).
Here, the first two octets defined the network, leaving 65,534 hosts, suitable for large universities or corporations. But still wasteful for smaller entities.
- Class C began with 110 (e.g., 192.0.0.0 to 223.255.255.0).
- Default mask: 255.255.255.0 (/24).
How CIDR Solved Classful Addressing Limitations
Only 254 hosts were allowed per network, which was too restrictive for mid-sized businesses.
CIDR eliminated this inefficiency by allowing variable-length subnet masks (VLSM). VLSM allowed for flexible adjustment of the division between network and host portions.
In CIDR notation, we represent the subnet mask with a slash followed by a number (e.g., /24). This indicates how many bits in the IP address the network portion uses.
The remaining bits are for hosts. This is more concise than writing out the full dotted-decimal mask (like 255.255.255.0) and directly shows the network’s granularity. For example:
- 192.168.1.0/24 means the first 24 bits are the network, leaving 8 bits (2⁸ = 256 addresses) for hosts.
- 10.0.0.0/8 reserves only the first 8 bits for the network, allowing over 16 million hosts (2²⁴).
- 172.16.128.0/18 (from the earlier example) uses 18 network bits, creating larger subnets than a /24** but smaller than a /16.
This shift from classful to classless addressing gave administrators finer control over IP allocation.
For instance, a company with 500 devices no longer had to take a whole Class B network (wasting ~65,000 addresses).
With CIDR, it could just use a /23 (512 addresses).
Similarly, IPv6 exclusively uses CIDR notation (like 2001:db8::/32) because its vast address space requires efficient segmentation.
Difference Between Subnet vs Subnet Mask
Many people use the terms “subnet” and “subnet mask” interchangeably. However, this is a mistake.
These two terms, while related, have different meanings.
A subnet, short for subnetwork, is a subdivision of a larger network created to group devices into smaller, isolated segments. You create subnets through a process called subnetting (more on this in the next heading).
In contrast, a subnet mask is a number that defines how to split an IP address between the network and host portions. This number essentially acts as a “rulebook” for determining which subnets exist and where devices belong.
A subnet cannot exist without a subnet mask because the mask creates the subnet by defining its boundaries.
You may think of it like a neighborhood (subnet) and its zoning laws (subnet mask). The laws dictate where houses (hosts) can be built, but the neighborhood is the physical result.
To put it simply:
- The subnet is the actual partitioned network (e.g., 192.168.1.0/24 is a network that can accommodate 254 hosts).
- The subnet mask is the mechanism that creates and enforces these partitions (e.g., 255.255.255.0 or /24).
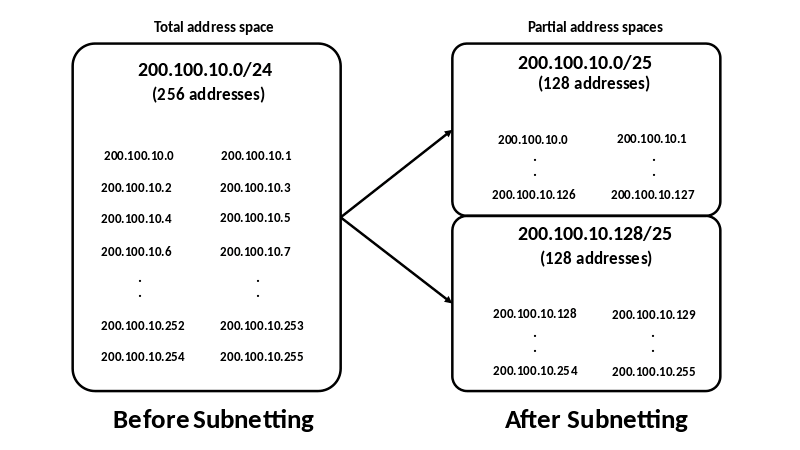
What Is Subnetting & How To Do It?
To explain subnetting and demonstrate how to perform it, I will use an example.
Imagine you run a small business, say a design agency, with 12 computers.
Your business has three departments: Design, Sales, and HR.
Each team needs its own private network space so that its data stays within its circle. Right now, everyone is on the same network, sharing all traffic. That’s chaos, and we don’t want that.
So, to fix this, we perform a process called subnetting.
Subnetting is a fancy term for breaking one big network into smaller and more manageable ones called subnets.
To subnet a network, we borrow bits from the host part and add them to the network part. This lets us divide that one big network into smaller ones.
Now, let me show you how to apply subnetting to our scenario.
Step 1: Define the Goal
Let’s say your IP address is 192.0.2.130. And the default subnet mask is 255.255.255.0 (which is 24 bits long, commonly written as /24).
This default setup gives you 1 network with up to 254 usable host addresses. Why not 256? Because you always lose two: one for the network address and one for the broadcast.
But we only need 3 smaller networks for our 3 departments. So, how do we do it?
Step 2: Borrow Host Bits
We need at least 3 subnets, but subnetting always gives us powers of 2.
So, to get at least 3, we need to borrow 2 bits from the host portion.
Why 2 bits? Because 2 bits gives us 2² = 4 subnets. That’s one more than we need, but hey, extra is good.
By borrowing those 2 bits, our subnet mask changes. Originally, the last octet (the fourth one) in binary was:
- 00000000 (which equals 0)
Now we change the first 2 bits in that octet from 0 to 1:
- 11000000 = 192 in decimal
So our new subnet mask becomes 255.255.255.192 or /26 in CIDR notation.
This change gives us 4 subnets, and each subnet can now hold 62 usable hosts (64 total addresses minus 2 reserved ones).
Step 3: Divide the Network
With a /26 mask, the 192.168.1.0 network splits into 4 subnets:
| Subnet # | Network Address | Usable Host Range | Broadcast Address |
| Subnet 1 | 192.0.2.0 | 192.0.2.1 – 192.0.2.62 | 192.0.2.63 |
| Subnet 2 | 192.0.2.64 | 192.0.2.65 – 192.0.2.126 | 192.0.2.127 |
| Subnet 3 | 192.0.2.128 | 192.0.2.129 – 192.0.2.190 | 192.0.2.191 |
| Subnet 4 | 192.0.2.192 | 192.0.2.193 – 192.0.2.254 | 192.0.2.255 |
From this breakdown, you can pick three subnets, one for each department. For instance:
- Design team lives in Subnet 1.
- Sales chills in Subnet 2.
- HR keeps to themselves in Subnet 3.
And just like that, each department now has its own subnet. Their traffic stays private, they won’t step on each other’s toes, and your network is now cleanly organized.
How Do Organizations Choose IP Ranges for Their Networks?
Alright, let’s talk about how organizations pick their IP address ranges because they cannot just pick any.
A small company doesn’t need a flood of IP addresses, while a global ISP definitely isn’t getting by on 254 hosts.
First off, IP addresses come in classes, which basically just help group networks by size. These are Class A, B, and C for commercial use. Classes D and E are for government stuff and experiments, so we won’t cover them in this guide.
Each class has a default subnet mask and a fixed range of IP addresses.
Here’s a quick rundown:
| Class | First Octet Range | Default Subnet Mask | Usable Hosts (Approx.) |
| A | 1 – 126 | 255.0.0.0 | ~16 million |
| B | 128 – 191 | 255.255.0.0 | ~65,000 |
| C | 192 – 223 | 255.255.255.0 | 254 |
So, how does an organization pick one? It depends on the number of hosts (i.e., devices like computers, printers, and coffee machines with IPs) they plan to have on their network.
Let’s jump into a scenario to make this crystal clear.
A Scenario
Byte-Sized Bakery is a growing business that started out baking cookies but now runs:
- Three bakeries
- A central warehouse
- And a small office
They’ve got around 80 devices across the company, including:
- Point-of-sale systems
- Cameras
- Computers
- And a couple of Wi-Fi fridges that send passive-aggressive alerts
Now, they want to segment their network to improve performance and security. Their goal is to divide their 80 devices into 3 smaller networks:
- One for the storefronts
- One for the warehouse
- And one for the office/admin staff
Because their total number of devices is under 254, a Class C IP range is perfect. It’s affordable, manageable, and totally adequate for their needs.
Other Factors When Choosing IP Ranges
In the real world, organizations also consider a few other factors when choosing IP ranges:
- Scalability: Will this range still work as the company grows?
- Security: Segmenting networks helps reduce risks. One infected coffee machine doesn’t bring down your whole operation.
- Addressing policies: Companies often use private IP ranges (like 10.x.x.x, 172.16.x.x – 172.31.x.x, or 192.168.x.x). Why? To avoid conflicts with public internet IPs.
- Routing simplicity: Neatly segmented networks make life easier for the network engineers who manage routing and firewalls.
What Is The Purpose Of A Subnet Mask & Subnetting?
By now, we have understood what is a subnet mask and the concept of subnetting. But what is the purpose of a subnet mask exactly? The following are the main reasons.
Routing & Network Identification
A subnet mask helps devices and routers figure out whether an IP address belongs to the same network or a different one.
Before the invention of CIDR (Classless Inter-Domain Routing), networks relied on classful IP addressing. Your IP address’s first few bits would tell whether it was Class A, B, or C. From that, devices could figure out what part of the IP referred to the network and what part referred to the host.
But CIDR came along and tossed that rigid system aside. Now, networks define their own subnet masks instead of being trapped in fixed classes.
So now, when a device wants to communicate with another, it uses the subnet mask in conjunction with the IP address to determine where the message should go. Here’s how it works:
- A device takes its own IP address and subnet mask and calculates the network address.
- Then, when it wants to send data to another IP, it calculates the destination’s network address using the same mask.
- If the two network addresses match, the device knows the destination is local and sends the message directly.
- If not, it punts the message to the default gateway, usually a router, which then handles the journey from there.
Breaking Down Large Networks for Manageability (Subnetting)
When all devices are on the same network, communication between any two of them often involves broadcasting.
That means sending messages out to everyone and hoping the right recipient answers. It’s kind of like yelling in a crowded mall, hoping your friend hears you.
And when hundreds or thousands of devices are all broadcasting at once? You get chaos. Network traffic slows, problems become hard to trace, and everything generally becomes a mess.
Subnetting fixes this by chopping large networks into smaller, isolated networks called subnets. Routers separate these subnets and don’t let random broadcasts through. Only the necessary data gets routed to other networks, and everything else stays nice and quiet.
So when a device tries to communicate with another device, it first checks within its own small subnet. If the device doesn’t exist in the local network, the broadcast travels outside the network to other routers and checks the routing table for the destination address.
If a router’s destination table has the recipient’s address, only then does the router let the broadcast in and send it to the respective recipient.
Enhancing Network Security (Subnetting)
In enterprise networks where thousands of devices are interconnected and sensitive data is constantly on the move, subnetting limits the damage if things go sideways.
Imagine your network as a big mansion, and subnets as individual locked rooms. If a burglar (a.k.a. a hacker) breaks into one room, they can only cause trouble in that space.
The rest of the mansion is still secure. That’s exactly what subnetting does. It segments the network into isolated chunks. If one subnet is compromised, the hacker’s view is limited to just that subnet. They can’t see or interact with devices in the other subnets without breaching more layers.
Beside isolation, subnetting also works hand in hand with other security tools to form a layered defense. Here’s how:
- Access Control Lists (ACLs): They decide who’s allowed in or out based on defined rules.
- Route Maps: These help steer traffic smartly, ensuring sensitive data doesn’t pass through risky or exposed routes.
- Quality of Service (QoS): This ensures that mission-critical applications (like your security monitoring system) always get top priority, even when the network is busy.
Conserving IPv4 Addresses (Subnetting)
When the creators created IPv4, they probably didn’t expect that one day, even your fridge would need an IP address.
But here we are: smartphones, smart TVs, smart toasters, each one wanting its own IP address. And with only about 4.3 billion IPv4 addresses to go around, that address pool started looking real thin.
Subnetting helped stretch the IPv4 pool.
Originally, IP addresses were doled out rather generously. An organization might get a whole block of addresses, even if it only needed a few. But subnetting allowed administrators to split a single IP block into multiple smaller networks.
That way, dozens or even hundreds of devices could share a common network identity without each one needing a separate public IP address.
Here’s a quick look at what this might look like:
- A business gets a public IP: 203.0.113.1
- Internally, they subnet their network using private IP ranges like 192.168.1.0/24, 192.168.2.0/24, etc.
- Each subnet has its own range of private IPs (e.g., 192.168.1.1 to 192.168.1.254)
- All outbound traffic from these subnets goes through that one public IP
This is how subnetting allows networks to support many more devices without needing more public addresses.
In a way, subnetting helped stave off the exhaustion of IPv4 address space, buying the world time to slowly roll out IPv6, which has more addresses to be enough for a long time.
Use GeoPlugin To Monitor IP Address Activity
By now, you must have understood what is a subnet mask and how subnetting facilitates network management.
But securing your network in real time requires more than just theory.
That’s where services like GeoPlugin come in handy.
GeoPlugin provides an IP geolocation API that helps you investigate IP addresses interacting with your systems. It can provide detailed information about any IP, such as geographic location, ISP, and even whether it’s part of a suspicious range or a bogon address.
By integrating GeoPlugin, you’ll be better equipped to monitor access, control traffic intelligently, and strengthen your subnet-level defenses. All using a single GeoPlugin API!
So, what are you waiting for? Sign up for GeoPlugin’s easy-to-use API today and be aware of your network traffic.
FAQs
Here are some of the frequently asked questions about what is a subnet mask IP address.
What is my subnet mask?
To find your subnet mask:
- Router: Log in to your router’s admin panel (usually via 192.168.1.1) and check the LAN settings.
- Windows: Open Command Prompt and type ipconfig. Look for “Subnet Mask” under your network adapter.
- Mac/Linux: Open Terminal and type ifconfig (or ip a on Linux). The subnet mask appears as “netmask” or “subnet.”
How to figure out subnet mask from IP address?
If you know the IP’s CIDR notation (e.g., /24), the subnet mask is:
- /24 → 255.255.255.0
- /16 → 255.255.0.0
- /8 → 255.0.0.0
For classful IPs (e.g., 192.168.x.x), the default is usually 255.255.255.0.
What is a subnet mask for wifi?
So, what is a subnet mask for WiFi? Your Wi-Fi subnet mask defines the local network’s size (e.g., home networks often use 255.255.255.0). To check it:
- On a router: See the LAN/DHCP settings in the admin panel.
- On a phone/tablet: Go to Wi-Fi settings, tap your network, and check “Subnet Mask” under advanced details.