In the 18th century, sending a letter involved including a return address. If someone sent a letter pretending to be you, they would use your address, even though they weren’t you. Similarly, IP spoofing tools manipulate data packets on the internet by changing the source IP address. It then appears that the data is coming from a trusted source.
These tools exploit the trust relationships that the internet protocol (IP) defines between the sender and receiver of the information.
The Internet Protocol is a set of rules governing the format of data sent over the Internet. It ensures that data reaches the correct destination.
This article explores IP address spoofing and how it works, and it introduces some common IP spoofing tools. Let’s start with the basics!

Table of Contents
What Is IP Spoofing?
To understand how spoofing of IP actually works, you first need to understand data packets and their components.
Data Packets and Their Components
When you send information over the Internet (emails, online messages, etc), it travels in smaller pieces called data packets.
Each packet has two main parts: the payload and the headers. The payload contains the actual information the source wants to send.
The headers contain essential information for delivering the packet, such as the source and destination IP addresses and sequencing information.
The source address is the IP address of the device sending the packet. Likewise, the destination IP address identifies the device receiving the packet.
This is where IP address spoofing takes place.
IP Spoofing
In IP spoofing attacks, the perpetrator alters the original data packets with a fake source address. Instead of the true sender’s IP address, the packet has a different address.
When these incoming packets arrive, the receiving device believes they came from the spoofed address. This can confuse the receiving system and allow the IP spoofer to carry out unauthorized actions.
For instance, the attacker can carry out the following attacks:
- Denial of service (DoS) attacks: Attackers flood a target with fake internet traffic to overwhelm it and cause it to crash.
- Man-in-the-middle attacks: Attackers intercept and alter communications between two parties. They make both parties think they are still communicating directly with each other.
- DNS spoofing: Attackers redirect traffic from a legitimate website to a fake one by sending spoofed packets to a DNS server.
These attacks can disrupt internet traffic, steal sensitive information, or take control of systems.
However, IP spoofing also has ethical use cases. Security experts can use IP spoofing tools for purposes such as:
- Network testing: Security experts use IP spoofing to test network defenses. By simulating spoofing attempts, they find and fix vulnerabilities.
- Research: Researchers study IP spoofing attacks to understand and develop countermeasures.
- Bypassing restrictions: Sometimes, people use IP spoofing tools to bypass regional internet restrictions. This can help them access unavailable or geoblocked content in their country.
Now, let’s explore some good IP spoofing tools for Windows and Linux.

Common IP Spoofing Tools for Windows
Here are a couple of IP spoofing tools that testers commonly use on Windows:
Wireshark
Wireshark is a popular IP address spoofing tool for observing and analyzing internet traffic. It helps during the packet sniffing stage of IP spoofing.
Wireshark lets you monitor data packets across private networks to help network specialists identify vulnerabilities. It can identify unusual traffic patterns and monitor bandwidth usage to detect potential DDoS and man-in-the-middle attacks.
Moreover, it can also help reveal vulnerabilities such as open ports and unencrypted sensitive information.
Netcommander
Netcommander is one of the common IP spoofing tools for creating and sending spoofed packets. It lets users create custom packets, modify fields like the source IP, and send the packets to the target. NetCommander also monitors the network for incoming packets to analyze responses to spoofed packets.
Security experts use NetCommander to simulate attacks and identify vulnerabilities. By crafting spoofed packets, they test how networks respond to a spoofing attempt. This helps strengthen network defenses and understand potential attack vectors.

Free IP Spoofing Tools for Kali Linux
Kali Linux users can consider the following tools for ethical IP spoofing.
Mitmproxy
Mitmproxy is one of the free IP spoofing tools that acts as a proxy server for intercepting and analyzing internet traffic.
When a device on a private network communicates with a server, Mitmproxy captures these packets. Users can then modify the source address or other packet details before forwarding them to the server. This helps in testing how the server responds to spoofed packets.
Mitmproxy’s interactive console lets users view, modify, and replay requests and responses. It supports various protocols, including HTTP, HTTPS, and WebSockets.
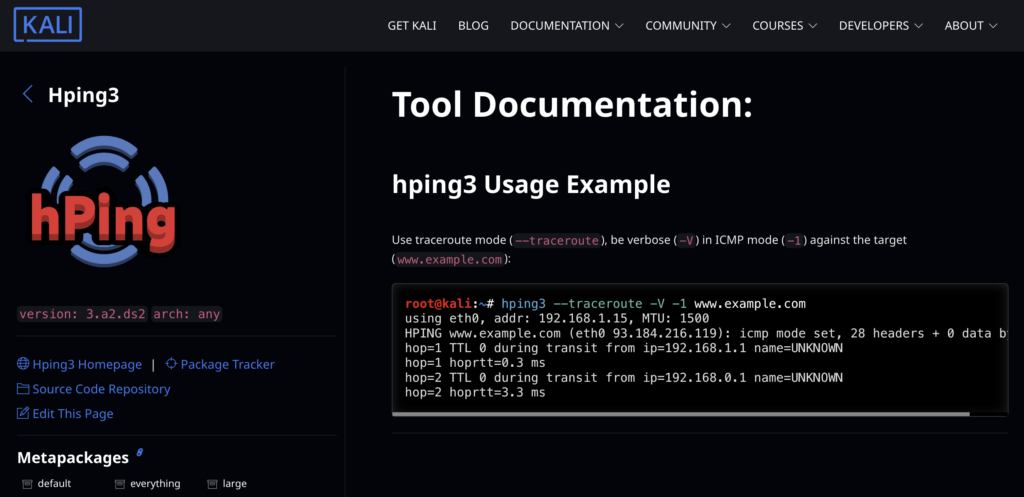
Hping
Hping allows users to create custom TCP/IP packets, send packets with specific flags, and analyze responses. It can also handle fragmented packets and perform traceroute-like path analysis. This tool is particularly useful for testing trust relationships within networks and identifying security weaknesses.
Hping exists as a software package compatible with various operating systems, including Linux, Windows, and macOS. It works in command-line and script-based applications.
How To Implement IP Spoofing Attacks (for Ethical Reasons)
To ethically perform an IP spoofing attack, security experts use the following approach:
- Gather necessary tools: You need reliable IP spoofing tools to create and send spoofed packets.
- Identify the target: Find the target’s IP address. You can use an IP geolocation database to gather information about the network.
- Monitor network traffic: Use packet sniffing tools to capture data packets on the network to understand the communication patterns.
- Create spoofed packets: Use an IP spoofing tool to create packets with a fake source address.
- Send spoofed packets: Send these spoofed packets to your target. The target will think the incoming packets are from a legitimate source.
- Intercept responses: If necessary, use ARP spoofing to intercept responses and see how the target reacts.
- Test and analyze: Once the target accepts the spoofed packets, analyze the results. Look for vulnerabilities in private networks and assess the effectiveness of your IP spoofing attacks.
How To Choose the Best IP Spoofing Software
Stick to the following guidelines when looking for good IP spoofing software:
- Packet customization: The best IP spoofing software allows custom packet creation for detailed IP spoofing attacks.
- Compatibility: Ensure the tool works with your operating system and supports private networks.
- Real-time analysis: Choose IP spoofing tools with real-time traffic monitoring.
- Protocol support: The software should handle various protocols, including HTTP, HTTPS, and DNS.
- Security testing features: A good IP spoofing tool lets you simulate all common network attacks, such as man-in-the-middle attacks, DDoS, and DNS Spoofing.
- User interface: A user-friendly interface simplifies the spoofing process.
- Community support: Strong community support indicates reliable and regularly updated tools.
FAQ
Can you detect IP spoofing?
While detecting IP spoofing is challenging because it occurs at the network level, it is still possible to detect it.
What is the main reason for IP spoofing
The main reason for IP spoofing is to mask the original source of the IP address. Users spoof IPs for both ethical testing and malicious activities.
Get IP Data From geoPlugin!
Both IP spoofing and defending against IP spoofing attacks often require a database or set of IP addresses. For IP spoofing, the database helps identify legitimate IPs to blend in with normal traffic and avoid detection.
Security experts need this database to maintain lists of trusted (whitelist) and untrusted (blacklist) IP addresses. The database also helps in anomaly detection, i.e., identifying IPs that don’t match expected patterns or regions.
So, while looking for IP spoofing tools, also find a good IP geolocation service to build an IP database.
Speaking of good geolocation services, you might like geoPlugin, a free and trusted IP geolocator. Using geoPlugin, you can analyze internet traffic and determine the country, zip code, and other IP details.
So sign up for geoPlugin today and conduct ethical IP spoofing like a pro!